Forcepoint Stonesoft Next Generation Firewall
Highly Available, Scalable and Flexible Protection Against Advanced Threats
Overview:
Environment Options

Appliance
Forcepoint Stonesoft Next Generation Firewall protects enterprise networks with high-performance "intelligence aware" security supported by real-time updates. This enables Stonesoft to deliver the industry's best defense against advanced evasions, along with complete next-generation firewall protection when and where you need it at remote sites, branch offices, data centers, and the network edge.
Forcepoint Stonesoft Next Generation Firewall (NGFW) starts with a solid foundation of protection, including granular application control, an intrusion prevention system (IPS), built-in virtual private network (VPN), and deep packet inspection, all in an efficient, extensible, and highly scalable unified design. Then we add powerful anti-evasion technologies that decode and normalize network traffic — before inspection and across all protocol layers — to expose and block the most advanced attack methods.
Block Sophisticated Data Breach Attacks
Large data breaches continue to plague businesses and organizations across industry verticals. Now you can fight back with application layer exfiltration protection. This new solution enables Stonesoft NGFW to selectively and automatically block network traffic originating from PCs, laptops, servers, file shares, and other endpoint devices based on highly granular endpoint contextual data. Application layer exfiltration protection is the only solution that goes beyond typical next-generation firewalls to prevent attempted ex-filtration of sensitive data from endpoints via unauthorized programs, web applications, users, and communications channels.
Superior flexibility keeps pace with your changing security needs
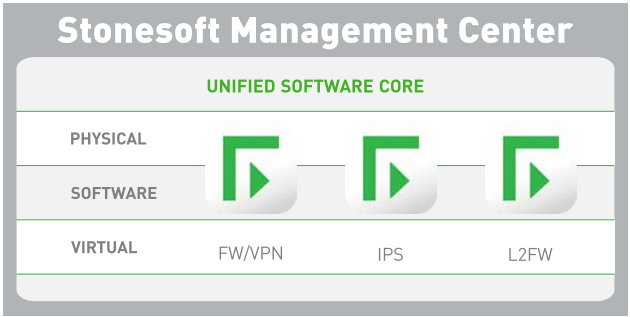
A unified software core enables Stonesoft NGFW to easily change security roles, from firewall/ VPN to IPS to layer 2 firewall, in dynamic business environments. The unified software core also serves to optimize the data plane, providing a significant performance advantage regardless of security role or number of active security features. For even more flexibility, Stonesoft NGFW can be deployed in a wide variety of formats — as a physical appliance, software solution, virtual appliance, or as virtual contexts on a physical appliance.
High scalability and availability secures your business-critical applications
Today’s businesses demand fully resilient network security solutions. Forcepoint Stonesoft NGFW delivers high scalability and availability in three powerful ways:
- Native active-active clustering: Up to 16 nodes can be clustered together, providing superior performance and resiliency when running demanding security applications, such as deep packet inspection and VPNs.
- Transparent session failover: Provides industry-leading availability and serviceability of security systems. Stonesoft NGFW even supports transparent failover for multiple software and hardware versions within the same cluster.
- Multi-Link: Extends high availability coverage to network and VPN connections. Provides the confidence of non-stop security along with high performance for every deployment.
Unmatched protection keeps your business in business
Every day attackers get better at penetrating enterprise networks, applications, data centers, and endpoints. Once inside, they can steal intellectual property, customer information, and other sensitive data, causing irreparable damage to businesses and reputations.
Some attackers use advanced evasion techniques (AETs) that are able to bypass most of today’s security network devices. AETs deliver malware piecemeal across network layers or protocols using techniques such as masking and obfuscation. Once inside networks, threats are reassembled where they can hide, exfiltrating sensitive data for days, months, or even years.
Forcepoint Stonesoft NGFW applies layered threat discovery techniques to network traffic, identifying applications and users at a granular level so that security policies can be applied according to business rules. Then it performs specialized deep packet inspection, including advanced techniques such as full stack normalization and horizontal data stream-based inspection. These techniques fully normalize traffic flows, enabling Stonesoft NGFW to expose AETs and traffic anomalies that evade other next-generation firewalls. Only after traffic has been fully normalized can it be properly inspected across all protocols and layers for threats and malware. And only Stonesoft NGFW has been successfully tested against more than 800 million AETs.
Features and Benefits:
Benefits
- The best protection for your business and digital assets
- Blocks endpoint data exfiltration attempts
- Adapts easily to your security needs
- Scales effortlessly as your business grows
- Optimizes productivity of employees and customers
- Lowers TCO for security and network infrastructure
- Delivers superior protection against advanced evasion techniques (AETs)
- Gives you holistic visibility into traffic and security across your distributed network
- Offers granular and flexible access controls, with optimized workflows to make life easier for your IT security team
- Reduces security-related downtime by 94%, with no scheduled downtime required for software upgrades
- Maintains high performance even with all next-generation firewall (NGFW) functions active
- Improves response time by 84%
- Reduces network infrastructure costs by 30%
Features
- Centralized management of up to 2,000 firewalls
- Built-in active-active clustering that scales to 16 nodes for high availability
- Plug-and-play installation of remote network firewalls
- Scalable and resilient Multi-Link VPN for site-to-site connectivity
- “Intelligence-aware” security controls
- Application layer exfiltration protection
- Advanced evasion prevention
- Unified software core design
- Many options for security and network infrastructure
- Powerful centralized management
- Built-in IPsec and SSL VPN
Specifications:
| Stonesoft Next Generation Firewall Specifications | |
|---|---|
| Supported Platforms | |
| Appliances | Multiple hardware appliance options, ranging from branch office to data center installations |
| Software Appliance | X86-based systems |
| Virtual Appliance | VMware ESX, Oracle VM, and KVM support |
| Supported Roles |
|
| Virtual Contexts (NGF License only) | Virtualization to separate logical contexts (FW, IPS, or L2FW) with separate interfaces, addressing, routing, and policies |
| Firewall/VPN Functional Role | |
| General | Stateful and stateless packet filtering, circuit-level firewall with TCP proxy protocol agent |
| User Authentication | Internal user database, LDAP, Microsoft Active Directory, RADIUS, TACACS+ |
| High Availability |
|
| ISP Multi-Homing | Multi-Link: high availability and load balancing between multiple ISPs, including VPN connections, Multi-Link VPN link aggregation, QoS-based link selection |
| IP Address Assignment |
|
| Address Translation |
|
| Routing | Static IPv4 and IPv6 routes, policy-based routing, static multicast routing |
| Dynamic Routing | IGMP proxy, RIPv2, RIPng, OSPFv2, OSPFv3, BGP, PIM-SM |
| IPv6 | Dual stack IPv4/IPv6, ICMPv6, DNSv6 |
| SIP | Allows RTP media streams dynamically, NAT traversal, deep inspection, interoperability with RFC3261-compliant SIP devices |
| CIS Redirection | HTTP, FTP, SMTP protocols redirection to content inspection server (CIS) |
| IPsec VPN | |
| Protocols | IKEv1, IKEv2, and IPsec with IPv4 and IPv6 |
| Encryption | AES-128, AES-256, AES-GCM-128, AES-GCM-256, Blowfish, DES, 3DES1 |
| Message Digest Algorithms | AES-XCBC-MAC, MD5, SHA-1, SHA-2-256, SHA-2-512 |
| Diffie-Hellman | DH group 1, 2, 5, 14, 19, 20, 21 |
| Authentication | RSA, DSS, ECDSA signatures with X.509 certificates, pre-shared keys, hybrid, XAUTH, EAP |
| Other |
|
| Site-to-Site VPN |
|
| Mobile VPN |
|
| IPsec VPN (NGF License Only) | |
| Client-Based Access | Supported platforms: Android 4.0, Mac OS X 10.7, and Windows Vista SP2 (and newer versions) |
| Portal-Based Access | OWA and Intranet access via SSL VPN portal through a browser |
| Inspection | |
| Anti-Botnet |
|
| Dynamic Context Detection | Protocol, application, file type |
| Advanced Anti-Malware | Policy-based file filtering |
| Sandboxing | Support for McAfee Advanced Threat Defense |
| File Reputation | Classification from McAfee GTI cloud service or optionally from local McAfee Threat Information Exchange |
| Anti-Malware Engine | McAfee Anti-Malware engine. Scanned protocols: FTP, HTTP, HTTPS, POP3, IMAP, SMTP |
| Protocol-Specific Normalization/ Inspection/Traffic Handling3 | Ethernet, H.323, GRE, IPv4, IPv6, ICMP, IP-in-IP, IPv6 encapsulation, UDP, TCP, DNS, FTP, HTTP, HTTPS, IMAP, IMAPS, MGCP, Modbus/TCP, MSRPC, NetBios Datagram, OPC Classic, OPC UA, Oracle SQL Net ,POP3, POP3S, RSH, RSTP, SIP, SMTP, SSH, SunRPC, NBT, SCCP, SMB, SMB2, SIP, TCP Proxy, TFTP |
| Protocol-Independent Fingerprinting | Any TCP/UDP protocol |
| Evasion and Anomaly Detection |
|
| Custom Fingerprinting |
|
| TLS Inspection |
|
| Correlation | Local correlation, log server correlation |
| DoS/DDoS Protection |
|
| Reconnaissance | TCP/UDP/ICMP scan, stealth, and slow scan detection in IPv4 and IPv6 |
| Blocking Methods | Direct blocking, connection reset, blacklisting (local and distributed), HTML response, HTTP redirect |
| Traffic Recording | Automatic traffic recordings/excerpts from misuse situations |
| Updates |
|
| URL Filtering | |
| Protocols | HTTP, HTTPS |
| Engine | Webroot category-based URL filtering, blacklist/whitelist |
| Database |
|
| Safe Search | Safe search usage enforcing for Google, Bing, Yahoo, DuckDuckGo web searches |
| Management & Monitoring | |
| Management Interfaces |
|
| SNMP Monitoring | SNMPv1, SNMPv2c, and SNMPv3 |
| Traffic Capturing | Console tcpdump, remote capture through SMC |
| High Security Management Communication | 256-bit security strength in engine-management communication |
| Security Certifications | Common Criteria EAL4+, FIPS 140-2 crypto certificate, CSPN by ANSSI (First Level Security Certification USGv6) |
1 Supported encryption algorithms depend on license used.
2 Firewall/VPN role only.
3 See firewall license-related limitations.
Documentation:
Download the Forcepoint Stonesoft Next Generation Firewall Datasheet (.PDF)
