
Forcepoint Email Security
Most Complete Email Visibility and Protection

Sorry, this product is no longer available, please contact us for a replacement.
Click here to jump to more pricing!
Overview:
Most large scale cyberattacks originate from email, using advanced, coordinated tactics, such as socially engineered lures and targeted phishing. As these multi-stage threats blend web and email elements throughout attacks, they present a “Kill Chain” of opportunities to stop them before the breach occurs.
- Stop Ransomware and Other Threats
Forcepoint Email Security uses the Advanced Classification Engine (ACE) to identify threats ranging from annoying spam to advanced malware, phishing, and Business Email Compromise (BEC) attacks. - Block Data Theft With Content-Aware DLP
Advanced capabilities detect data theft concealed in images or custom-encrypted files, even when gradually transmitted in small amounts to evade detection. - Identify High-Risk User Behavior
The rich data collection capability can quickly generate a report on Indicators of Compromise to identify infected systems and suspicious user behavior.
Maximize your use and safety of email
Forcepoint Email Security identifies targeted attacks, high-risk users and insider threats, while empowering mobile workers and the safe adoption of new technologies like Office 365 and Box Enterprise.
From inbound attack activity to outbound data theft or botnet communication attempts, Forcepoint Email Security secures mixed environments with content aware defenses, protecting email communications as part of a complete and connected defense system against Advanced Persistent Threats (APTs) and other types of advanced threats.
Forcepoint Email Security capabilities
Stop APT and other advanced targeted threats
Forcepoint’s Advanced Classification Engine (ACE) is at the heart of all Forcepoint solutions. ACE identifies malicious lures, exploit kits, emerging threats, botnet communications and other advanced threat activity across the Kill Chain. This enables Forcepoint Email Security to identify the early stages of an attack. It can even identify Zero-day malware threats using powerful assessment capabilities that include fully-integrated, file behavioral sandboxing.
Secure sensitive data against external attacks and insider threats
To prepare for a malicious insider threat or the potentially successful cyberattack, it’s vital that outbound communications be monitored. This is also necessary both for data theft compliance needs as well as for business requirements. Only Forcepoint provides the technology to stop data infiltration and exfiltration with capabilities such as:
- OCR (Optical Character Recognition) scanning to identify sensitive data hidden in images such as scanned documents or screen shots.
- Encrypted file detection to recognize custom encrypted files designed to defy identification.
- Drip data loss prevention (DLP) monitoring to identify where sensitive data is leaked in small quantities over time.
- Advanced analysis of malicious files and macros typically embedded in with MS Office files.
Safely adopt cloud technologies like office 365 and box enterprise while supporting a mobile workforce
IT departments are strained to maintain current systems while supporting an increasingly mobile workforce and the demands to adopt new technologies like Office 365. Forcepoint Email Security provides industry-leading capabilities that leverage systems and other information to control communications, such as preventing total access to sensitive email attachments on vulnerable mobile devices, while permitting full access on fully-secured laptops. These inbound and outbound defenses are all supported on Office 365.
Identify "High-Risk" user behavior and educate users to improve awareness
The rich data collections in Forcepoint Email Security are used by a number of policies to report and identify systems that may require special IT attention. They generate a report on Indicators of Compromise to identify infected systems, and more proactive reports on suspicious behavior, including potential insider threats, such as “disgruntled employee” activity. User feedback capabilities educate employees as mistakes are made, helping them to better learn and understand safe email best practices.
Superior Email Protection for Microsoft Office 365
Forcepoint Email Security enhances built-in security capabilities to address inbound threats and outbound data loss risk. It’s one of the key parts of a complete, integrated Office 365 defense from Forcepoint.
The power behind Forcepoint solutions
Forcepoint ACE
Forcepoint ACE provides real-time, inline, contextual defenses for Web, Email, Data and Mobile security by using composite risk scoring and predictive analytics to deliver the most effective security available. It also provides containment by analyzing inbound and outbound traffic with data-aware defenses for industry-leading data theft protection. Classifiers for real-time security, data and content analysis — the result of years of research and development — enable ACE to detect more threats than traditional anti-virus engines (the proof is updated daily at http://securitylabs.forcepoint.com). ACE is the primary defense behind all Forcepoint solutions and is supported by the Forcepoint ThreatSeeker Intelligence.
Forcepoint ThreatSeeker Intelligence
The Forcepoint ThreatSeeker Intelligence, managed by Forcepoint Security Labs, provides the core collective security intelligence for all Forcepoint security products. Together with Forcepoint ACE security defenses, Forcepoint ThreatSeeker Intelligence analyzes up to 5 billion requests per day, and unites more than 900 million endpoints, including those from Facebook. This expansive awareness of security threats enables Forcepoint ThreatSeeker Intelligence to offer real-time security updates that block Advanced Threats, malware, phishing attacks, lures and scams, while simultaneously providing the latest web ratings. Forcepoint ThreatSeeker Intelligence is unmatched in size and in its use of ACE real-time defenses to analyze collective inputs. When you upgrade to Web Security, Forcepoint ThreatSeeker Intelligence helps reduce your exposure to web threats and data theft.
Unified Architecture
With best-in-class security and a unified architecture, TRITON Architecture offers point-of-click protection with real-time, inline defenses from Forcepoint ACE. The unmatched real-time defenses of ACE are backed by Forcepoint ThreatSeeker Intelligence and the expertise of Forcepoint Security Labs researchers. The powerful result is a single, unified architecture with one unified user interface and unified security intelligence.
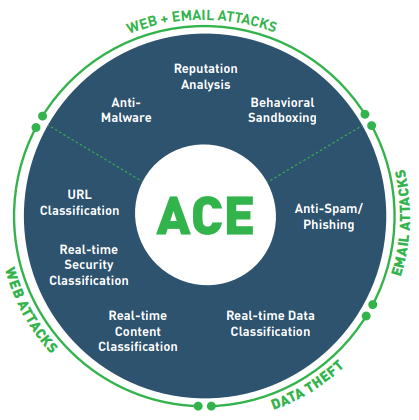
Integrated set of defense assessment capabilities in 8 key areas.
- 10,000 analytics available to support deep inspections.
- Predictive security engine sees several moves ahead.
- Inline operation not only monitors, but blocks threats.
Use Cases:
Control Device Access to Email Attachments
Prevent total access to sensitive email attachments on vulnerable unmanaged devices (BYOD) while permitting full access to secure managed devices.
Ensure Confidentiality of Sensitive Communications
Enable secure delivery of email communications with Forcepoint Email Encryption that eliminates the traditional barriers of cost and complexity by offering easy administration, without key management or additional hardware.
Identify Explicit Images to Enforce Acceptable Use
The Forcepoint Image Analysis Module allows employers to proactively monitor, educate, and enforce company email policy for explicit or pornographic image attachments.
Spam and Phishing Protection
Detect unwanted spam and unsafe phishing emails, allowing customers to block, quarantine, or take other actions.
Educate Users to Improve Security Awareness
Unique phishing education with feedback capabilities educates employees as they make mistakes, helping them to better learn and understand safe email best practices.
Features:
The Forcepoint Email Security Advantage
Real-Time Threat Protection
Real-time threat protection uses a unique blend of detection technologies, including machine learning, sandboxing, and predictive analytics to effectively stop advanced threats such as ransomware.
Powerful Encryption for Additional Protection
Encrypt sensitive email conversations and enhance mobile security by controlling sensitive attachments access by device.
Integrated Data Loss Prevention
Integrated industry-leading data loss prevention stops data infiltration and exfiltration capabilities.
Complete Out-of-the-Box Solution
Forcepoint Email Security includes DLP, URL wrapping, and other capabilities that are considered premium "add-ons" or upgrades by many competitors, delivering the most comprehensive inbound and outbound defenses out of the box.
Protection Against Highly Evasive Zero-Day Threats
Get advanced malware detection(sandboxing) with our full system emulation sandbox. Deep content inspection reveals highly evasive zero-day threat with no false positives.
Incident Risk Ranking to Find the Greatest Risks
Incidents are correlated across multiple events to identify true cumulative risk trends and activity. A risk score is included to help security teams identify the greatest risks based on real-time activity.
Unique Phishing Education Feature
Use Forcepoint Email Security’s unique phishing education features to help users adopt best practices and identify those who need additional training to improve their security awareness.
Deployment Flexibility
How you deploy our email security solution is up to you. Choose from a range of physical and virtual appliances to leverage existing hardware, cloud deployment, or hybrid environments.
Enhanced Protection Modules:
| Enhanced Protection Modules | |
|---|---|
| Optional Hybrid Cloud Deployment | Leverage Forcepoint’s global cloud services for performance and scalability Combine on premise threat defenses with cloud-based pre-filtering services to preserve bandwidth with industry-leading anti-spam SLA’s. The hybrid module adds URL Sandboxing and Phishing Education to the Email Security solution. |
| Email DLP | Block data theft with enterprise-class content-aware DLP Prepare for the insider threat and malware data theft, achieve compliance goals and further mitigate risks to personal information or IP. Advanced capabilities detect data theft concealed in images or custom-encrypted files, even when transmitted in small amounts over time to evade detection. |
| Cloud Sandbox | Integrate behavioral sandboxing for automatic and manual analysis of malware files Supplement Forcepoint ACE analytics with an integrated file sandbox for additional deep inspection. Take advantage of behavioral analysis in a virtual environment to uncover the malicious behavior of Zero-day and other advanced malware. Test files automatically or manually to generate detailed forensics. |
| Email Encryption | Ensure the confidentiality of sensitive communications The Forcepoint Email Encryption Module is a policy-driven technology that enables secure delivery of email communications. It eliminates the traditional barriers of cost and complexity by offering easy administration, without complex key management or additional hardware. |
| Image Analysis | Identify explicit images to enforce acceptable use and compliance The Forcepoint Image Analysis Module allows employers to take proactive measures to monitor, educate and enforce company email policy with regard to explicit or pornographic image attachments. |
Screenshots:
Documentation:
Download the Forcepoint Email Security Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.
