Forcepoint SureView Insider Threat
The Visibility and Context You Need to Eliminate Insider Threats
Sorry, this product is no longer available, please contact us for a replacement.
Click here to jump to more pricing!
Overview:
Environment Options

Appliance
Empower your organization to better protect the information entrusted to it by customers, citizens or other stakeholders by detecting your riskiest users and tracking the insider activities that could damage your organization.
“Trust, but verify.” You want to give your employees the latitude they need to do their jobs, but you also need visibility into their actions so you can protect your organization and the information entrusted to it by customers, citizens or others. Insider threats are often a greater risk than external attacks, and today many external attacks also turn into insider threats either by tricking the user or by silently subverting their browser or computer.
Most organizations know they need to take insider threats seriously, yet lack the resources or expertise to handle them effectively. Since 2001, the technology that powers SureView Insider Threat has made it possible for employers to stop insider threats through an objective, rigorous process of verification that captures all relevant data while respecting user privacy. Our technology connects the dots for you, capturing human behaviors arising from carelessness, lack of training or malicious intent that may be warning signs of an impending breach.
Historically, the term “insider threat” conjures up images of malicious employees creeping into dark offices, stealing company secrets in order to profit or create irreparable damage to the company. The truth is that this type of evil insider is rare, with instances of these types of threats occurring once in a decade or less. The real insider threat is the negligent employee A.K.A. the accidental threat. Negligent employees invite risk through uninformed, highly questionable behaviors. Via social media and email scams, adversaries target them, to con them into doing something that appears legitimate, but actually allows the adversary to slip “inside the gate” of the network. One-half of organizations view these staffers as their biggest threat.
Data Capture
SureView Insider Threat uses a lightweight endpoint agent to capture data without disrupting user productivity. The system monitors data’s location and movement, as well as the actions of users who access, alter and transport that data. This includes not only functions that directly affect the data, but telltale precursor actions that can signal a breach is coming. The system can even fingerprint your organization’s critical intellectual property and sensitive documents, enabling it to track the assets that you identify as most sensitive.
Collected user data can be viewed as a video replay that displays keys typed, mouse movements, documents opened or websites visited. This unique capability provides irrefutable and unambiguous attribution of end-user activity.
Behavioral Audit
Our deep experience protecting more than 1 million endpoints for government agencies and Fortune 100 companies means that we know what insider threats look like. That knowledge is embodied in SureView Insider Threat’s library of pre-defined policies, which allow you to stand up an effective insider threat prevention program right out of the box.
Our technology also baselines behavior to establish what is normal for each individual and for the organization as a whole. It then identifies deviations from that behavior, automatically placing risky users in a high-watch group for closer scrutiny. The system collates relevant information from across your enterprise and displays it in an intuitive, visual dashboard so that it can easily be reviewed and understood by even non-technical security personnel.
Focused Investigation
If a clear violation is detected, you can target specific events or users for investigation. SureView Insider Threat provides all the details, insight and complete context needed so your team can immediately assess the severity of the threat, remediate the problem and create new policies to prevent it from happening again.
SureView Insider Threat provides visibility into the many areas that network devices can't, including:
- Deliberate, malicious acts such as intellectual property (IP) theft, fraud or sabotage that easily circumvent most data leak solutions
- Mobile and internal users who take themselves offline or use encryption to avoid detection
- Suspicious user activity within complex applications, including email programs and custom deployments of Enterprise Risk Management (ERM) and other solutions
- “Leading indicator” actions, such as a screen capture that has been encrypted and saved to a USB drive
Unintentional Insiders: The Real Insider Threat
A lack of awareness accounts for much of the negligent employee’s behaviors, as 45 percent of workers receive no cybersecurity training on the job, according to CompTIA1 . Nearly two-thirds depend upon business-intended devices for personal activities like shopping, banking and social media surfing. Virtually all of them connect their devices to public Wi-Fi networks, with seven out of ten calling up company-related data while doing so. And when USB storage drives are involved, the results can be frightening.
The Unintentional Insider Threat
- Three-of-five employees rely upon potentially insecure USB storage drives to transfer files among devices.
- Thirty-five percent have borrowed someone else’s USB stick to transfer files.
- More than one-fifth would pick up a stick they found in public.
- An astonishing 84 percent of those who’d pick up a stick they found would plug it into one of their work devices.
Clearly, traditional security tools – while still playing a key role in safeguarding systems – no longer suffice as a sole remedy. Organizations need to match technology with human oversight, paving the way for 24/7/365 visibility into how users behave, no matter when or where they’re connecting to the network. Then, they have to prioritize each risk and launch remediation/mitigation measures.
See Threats Before They Become Disasters
SureView Insider Threat identifies risky behaviors by baselining “normal” for each user, the organization then captures deviations from “normal” such as: a change in data access, working hours, email activity etc. These deviations are risk indicators that serve as warning signs leading up to a breach. The riskiest users are pinpointed with deep visibility provided into their behaviors.
SureView Insider Threat’s integration and correlation with TRITON AP-DATA and multiple enterprise data sources provides enterprisewide visibility into how users handle data, to detect both unintentional insider threats and malicious activity, that would otherwise go unnoticed. Combining enterprise-wide data sources with behavior analytics does the investigating for you — providing insight into activity that, on its own, may seem benign, but in context could result in a costly breach.
SureView Insider Threat was designed as an insider threat solution starting in 2001. It is not, like some technologies, a solution retrofitted to the problem. The SureView Insider Threat team are domain experts who have spent their careers in information protection. Whether the incident is accidental or deliberate, or somewhere in-between, SureView Insider Threat gives you complete visibility and quickly identifies the riskiest users in your organization, all while preserving employee privacy guidelines.
Features and Benefits:
Benefits
- Tracks endpoint user and system activity
- Baselines “normal” activity across the organization
- Exposes and quantifies risk through user behavior analytics
- Enables investigation of anomalies with integrated, chronicled data sources
- Provides incident replay, including full-event endpoint video recording
- Detects policy violations hidden by encryption, whether in Web traffic, email or attachments
- Reduces dependency on technical expertise for your investigators
- Promotes education and remediation for accidental data leak prevention
- Integrates seamlessly with DLP capabilities in Forcepoint TRITON products
- Monitors offline activity for mobile and deliberately disconnected users
- Scales easily using a highly-stable endpoint agent
Features
- Trusted mission partner of government organizations and Fortune 100 companies since 2001
- Behavioral analytics discovers top riskiest users, and provides deep visibility into those behaviors, including past behaviors
- Video replay for full context to rapidly discern malicious from benign actions
- Protects Personal Privacy through customizable, business-driven policies
- Data collection from multiple sources, including TRITON AP-DATA
- Protects against unintentional insider threats as well as malicious threats
- Integrated, enterprisewide system rather than purchasing and maintaining a number of independent software applications
- Unique fingerprinting solution
- Proven, stable, lightweight Agent
- Built as an Insider Threat solution from the ground up
Capabilities:
The Command Center:
The command center provides analysts their organization’s risk level at a glance: it displays the organization’s overall 30-day risk trend and a summary of the day’s riskiest users.
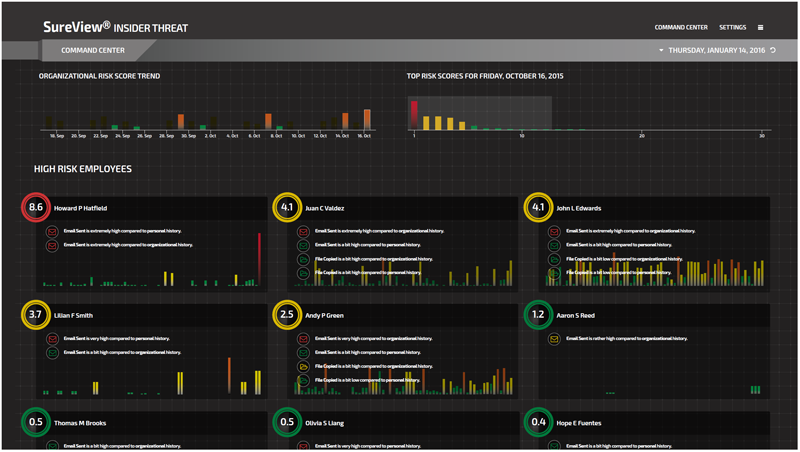
The Command Center - Organizations 30-Day Risk Trend
Video Replay:
Video replay provides complete, near-real-time context with an “over-the-shoulder” view of the end-user’s workstation. A security analyst can create a case and easily share data and replay with non-technical management or security personnel.
Identifying the Threat:
SureView Insider Threat comes with pre-configured policies identified by Forcepoint experts who have been implementing Insider Threat Programs for Fortune 100 and Government agencies since 2001. These policies are ready to protect your organization against the insider threat the day it is deployed.
Protecting Civil Liberties:
SureView Insider Threat policies are easily customized and created using The Policy Workbench or “policy wizard” and allows users to specify what information to collect and what information not to collect to preserve civil liberties and personal privacy.
Unique Fingerprinting Capabilities:
SureView Insider Threat features an extensive ability to fingerprint an organization’s critical intellectual property or sensitive document library. Most technologies simply hash these documents and compare the stored hash with files as they leave your network. This process is easily thwarted. A simple word change or even an extra period will significantly alter the hash value of the newly changed document. Therefore, typical detection methods require the entire document to be copied for detection while SureView Insider Threat can detect fractional movement from any part of a fingerprinted document. SureView Insider Threat is a point-ofuse discovery tool capable of capturing intentional and unintentional insider threats to an organization at the desktop/laptop level. This enables detection of abusive behaviors and capture of sensitive documents before encryption or deletion.
Light Footprint:
A distributed architecture reduces the processing load required to monitor an entire organization. Forcepoint SureView Insider Threat provides ongoing, automated visibility into accidental or malicious activity that otherwise goes unnoticed. It effectively consolidates and prioritizes security alerts sent from other systems and data sources, providing rich historical context and video replay. SureView Insider Threat acts as an “early warning system” to collect user data from all endpoints to pinpoint risky behavior. It records the activity for your review, giving you critical context and proof to stop threats before they become disasters.

Documentation:
Download the Forcepoint SureView Insider Threat Datasheet (.PDF)
Price Note:
- TRITON AP-DATA Discover, TRITON AP-DATA Gateway, TRITON AP-ENDPOINT DLP, Threat Protection Appliance - Endpoint, SureView Insider Threat Core and SureView Insider Threat Endpoint under 250 user band subject to approvals.
- Threat Protection Appliance - Web, Threat Protection Appliance - Email and Threat Protection for Linux under 100 user band subject to approvals.
