
Forcepoint Trusted Thin Client
Secure Enterprise Access to Multiple Domains From a Single Device

Click here to jump to more pricing!
Overview:
- Secure access to multiple sensitive networks
Gain simultaneous access to multiple classified networks or Virtual Desktop Infrastructure (VDI) Environments from a single endpoint device. - Lower total cost of ownership
Achieve significant return on investment (ROI) through lower ownership costs in infrastructure, office space, power consumption, and administration. - Designed to comply with Raise The Bar guidelines
Assessed and authorized according to NIST guidelines; in compliance with all National Cross Domain Services Management Office (NCDSMO) initiatives.
Enabling secure access to sensitive data, applications, and networks
Government agencies know better than most how pervasive and costly (in lives, trust and money) cyberattacks and breaches can be. One basic method of defense is to ensure complete compartmentalization and data separation through physically separate network architectures. This security best practice is commonly referred to as “network segmentation.” According to a recent Liberty Group Ventures white paper, network segmentation, while “[] it does not ensure that hackers “stay out” [] it keeps them in one place should they breach the perimeter. Damage is therefore contained [and] only one domino can possibly “fall,” not five, ten or 20,000. This is the essence of successful cyber risk management and resiliency.”
As agencies have discovered working in this secure-by-design environment has also led to high costs (hardware, power, and administration) and usability and endpoint security burdens by requiring one computer per network for each user.
This is no longer the case. Due to the increased adoption of virtualization to move desktop, application and data resources back into the datacenter and increased operating system security, the physical separation can be maintained while permitting secure simultaneous access to allowed networks from a secure endpoint device. Forcepoint Trusted Thin Client, delivers the most robust combination of security, flexibility, usability and reduced total cost of ownership available to enable secure access to multiple sensitive networks.
Forcepoint Trusted Thin Client
Forcepoint Trusted Thin Client is comprised of two components, a Distribution Console and client software. The Distribution Console is the solution’s server component and provides the physical connection to one or more single-level virtualized networks, maintaining separation between each.
The Distribution Console leverages the Common Criteria evaluated (EAL4+) Red Hat Enterprise Linux operating system with SecurityEnhanced Linux (SELinux) to provide stringent security controls and maintain the necessary network/data separation. The client software communicates directly with the Distribution Console and provides secure, simultaneous access to permitted networks, applications and data.
While providing connectivity to multiple security domains through common virtualization and desktop and application redisplay technologies (e.g., Citrix, Microsoft, VMware), each network has a separate physical network interface connection on the Distribution Console that is assigned the classification level of the domain. Security protections prevent data from being transferred between classification levels. The Distribution Console silently rejects all communications from unauthorized systems, reducing risk exposure to the enterprise.
Built for the enterprise
Designed and built to meet the needs of any enterprise deployment, Forcepoint Trusted Thin Client is the most secure yet flexible access solution available today, providing robust centralized management for multiple form factors, globally dispersed sites and thousands of users. Administrators are equipped with centralized administration and monitoring, scalability to easily add networks and clients, and the flexibility to enable access to users in offices, in-theater, and in the field from virtually any device.
Restricted, High-Risk Installation Environments
Environments that provide connection to high-risk networks, such as unclassified networks or the open Internet, are required to operate in a restricted manner. To enforce this requirement, Forcepoint Trusted Thin Client installation is modular based on your environment. Restricted, high-risk environments are installed with some features removed.
| Feature | SABI Availability | TSABI Availability |
|---|---|---|
| USB Peripheral Redirection (thumb drive, optical reader/writer, printer, scanner) | ||
| Video Playback through Multimedia Redirection (optimized) and Media Player application | *Video playback is available through Windows VDI sessions |
|
| HDX RealTime Optimization Pack for Lync - Skype for Business | *Skype for Business is available through Windows VDI sessions, non-optimized |
|
| Remote Distribution Console Administration via Private, Administration Network |
Central Administration Monitoring and Auditing
The Distribution Console is the solution’s administration and monitoring hub from which all Distribution Consoles, endpoints and users are administered through the Management Console application.
It is recommended that all deployments utilize multiple Distribution Consoles to address server outages, scheduled maintenance and unexpected hardware failures. Through the Management Console, administrators can administer any Distribution Console from any other Distribution Console in the enterprise – greatly reducing the need for on-site resources and the cost to transport administrators from site to site. Administrators configure clients to failover to redundant Distribution Consoles (on- or off-site) when necessary, allowing work to continue unabated.
The Distribution Console serves as a centralized audit repository for the client software to track use and activity. This audit data can be pushed to a centralized enterprise audit storage location.
Administrator Role and Account Separation
Additional security controls are provided through granular administrator role and account separation. Each account is permitted only one role on the system, thus enforcing the requirement that multiple personnel provide checks and balances for privileged actions, system changes and system data access.
Client User Management
The Distribution Console provides all necessary configuration information for client initialization and communication services. This information contains relevant security data and allows the user to access the virtual environments. When a network at another security level or a new server is added to the Distribution Console, the information is automatically sent to each client, removing the need to locally manage or update individual clients.
User access controls (username, password, and clearance level) are validated by the Distribution Console through either hosted Lightweight Directory Access Protocol (LDAP), external high-side LDAP, or external high-side Microsoft Active Directory. Utilizing a preexisting LDAP or Active Directory server eliminates the need to manage user accounts on the Distribution Console, further reducing administrative overhead.
Support for Multiple Endpoint Devices
In support of the variety of missions and users that make up an enterprise, the same client software can be implemented on different form factors: thin client hardware, PCs, laptop and hybrid devices, or a virtual machine resident on a host operating system. All recommended hardware is certified in-house by Forcepoint engineers. All endpoint devices run a read-only, stateless, SELinux multi-level secure (MLS) operating system that meets the most stringent security requirements. Users interact with the securityenabled and labeled (visual and code-based) graphical windowing system, which provides immediate access to simultaneous presentationlayer clients (Citrix, Microsoft, VMware) at one or more sensitivity levels on one or more monitors (up to 8, portrait and landscape orientation).
Risk exposure is greatly reduced due to the readonly device, strict network and virtual desktop session separation, and the fact that Forcepoint Trusted Thin Client only provides a redisplay of data from the data center. Should malicious code make its way to a virtual desktop, these factors prevent it from moving from one network to another greatly reducing the risk to the overall infrastructure.
Additionally, if a foreign or unapproved device is introduced to the client network, that device is prevented from communicating with the Distribution Console. The system is completely controlled and protected through the enforcement provided by the trusted operating systems on which the client and Distribution Console run and through the use of digital certificates.
Assessment and Authorization (A&A)
Forcepoint Trusted Thin Client is recognized by the US Unified Cross Domain Services Management Office (UCDSMO) and is included on the UCDSMO Baseline List. Forcepoint Trusted Thin Client is designed and developed to meet or exceed National Institute of Standards & Technology (NIST) 800-53 and 800-37 (SP), the Committee for National Security Systems (CNSS) Instruction 1253 requirements, and the Risk Management Framework (RMF) as required by Intelligence Community Directive (ICD) 503 and Department of Defense (DoD) IT for securing the most sensitive information. Forcepoint Trusted Thin Client has been assessed and authorized by authorities in the US – Top Secret/SCI and Below Interoperability (TSABI) and Secret and Below Interoperability (SABI) – and Five-Eyes nations.
Use Cases:
Improve staff efficiency on mission-critical workflows
Save time while accessing multiple resources from a single workstation. Reduce total head count and avoid unnecessary transitions between hardware devices.
Network and client scalability
Implement in traditional office environments, large operations centers, in the field, in-theater, forward operating bases, in tactical vehicles, ship and aloft—anywhere critical data must be accessed and shared.
Dynamic network configuration
Tear down or stand up new “mission” networks when needed and without service interruption via rapid, real-time network configuration.
Flexible use cases and environments
Implement anywhere critical data must be accessed (e.g., office, in-field, in-theater).
Broad authentication support
Supports Common Access Card (CAC), SAC, and SIPRtoken smartcards for identity management and access authorization to back-end Microsoft Windows servers.
Commercial Off-The-Shelf (COTS) solution
Built and supported by proven development, support, and professional services teams.
Features:
A secure access solution with support for one or many globally dispersed sites
Distribution console
Distribution console provides physical connection to one or more single-level virtualized networks, maintaining separation between each.
Scalability
Support up to 20 networks and 400 terminals/endpoints per Distribution Console.
Endpoint device flexibility for your environments
Implement client software on a virtual machine residing on a host operating system or on other mediums (e.g., thin client hardware, PCs, hybrid devices).
Multi-monitor support
Supports up to eight monitor displays—unmatched by other access solutions.
Commercial Solutions for Classified (CSfC) program
Architecturally enabled to support the CSfC program adhering to NSA’s cybersecurity and assurance strategy.
Single, read-only operating system
Keeps data from being stored locally, transferred, or copied to an external device. Client image is a centrally managed, 64-bit encrypted image.
Expand or contract deployment quickly
Supports VLAN networks for services, enabling admins to change existing clusters with zero impact to users and minimal administrative overhead.
High availability
Multiple Distribution Consoles can be clustered together to provide high availability access to critical resources.
Redisplay technology agnostic
Provides connectivity to multiple security domains through common virtualization and application redisplay technologies (e.g., Citrix, Microsoft, VMware).
Accredited
NCDSMO-approved for 10+ years.
Benefits:
- Assessed and Authorized by authorities according to NIST guidelines in the US and FiveEyes nations
- Supports DoD and IC VDI initiatives such as DoD Joint Information Environment (JIE)
- Commercial-Off-The-Shelf (COTS) solution
- Simultaneous access to multiple networks/clouds from a single endpoint
- Significant ROI through lower ownership costs (infrastructure, office space, power consumption and administration)
- Maximized security, usability and adaptability
- Flexible implementation options to meet the needs of your organization
- Streamlined administration through robust enterprise management capabilities
- Supports a wide array of hardware; agnostic for both servers and endpoint devices
- Redisplay technology agnostic (Citrix, Microsoft, VMware)
- Supports the use of Common Access Card (CAC), SAC and SIPRtoken smartcards for identity management and access authorization to back end Microsoft Windows servers
- Supports Suite B cryptographic algorithms for all encrypted communications on the client network
Deployments:
Forcepoint Trusted Thin Client Architecture
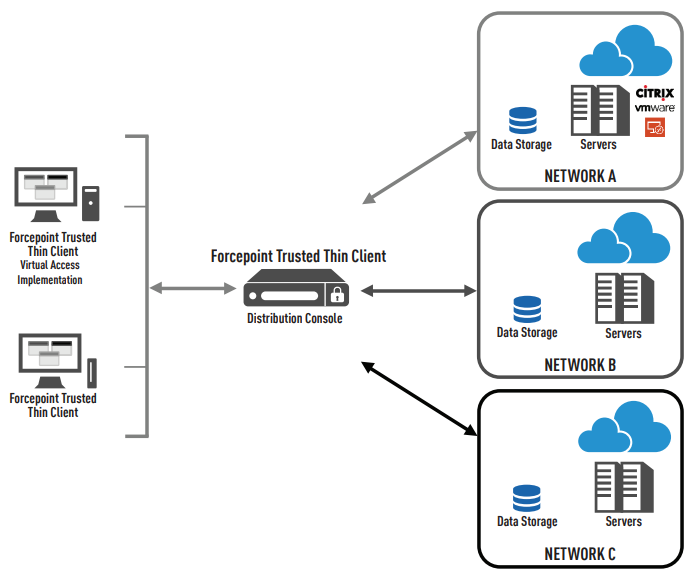
Forcepoint Trusted Thin Client Distribution Console Spanning
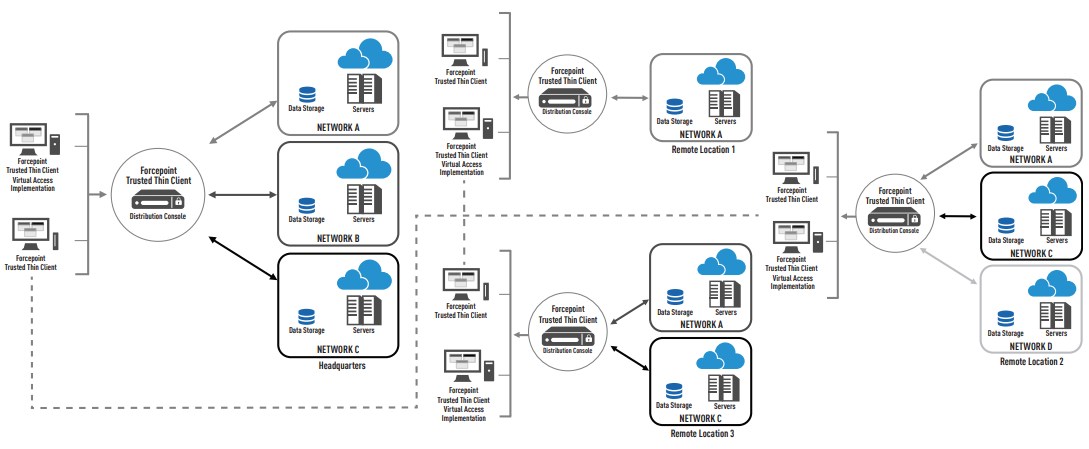
Documentation:
Download the Forcepoint Trusted Thin Client Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.
